Cyber Security Data Analytics Solutions
Why rely on analyzing threat signals at scale, strengthening defenses and readiness?
Stronger Security Through Data Innovation
We are cyber security data experts dedicated to helping organizations make smarter, faster, and more accurate decisions through insightful analytics and AI-assisted defenses. From strengthening threat detection to streamlining incident response, our solutions are designed to provide lasting protection across your digital ecosystem.
We take our mission seriously but never forget to stay adaptable. Because robust security starts with powerful data, and powerful data starts with a team that’s vigilant.
Let’s fortify security together.
Our Cyber Security Experience Will Maximize Your Security Data’s Value

Security Centric Strategy Consulting
Address complex cyber risks and vulnerability obstacles with our specialized consulting services. Leverage our deep security expertise and threat-centric view to develop, implement, and scale solutions that directly fortify your defenses.

Designing Personalized Security Platforms
Out-of-the-box solutions often miss unique enterprise needs. We craft tailored security platforms from vulnerability scoring to incident orchestration ensuring smooth integration across your digital ecosystem.

Turning Security Data into Actionable Insights
Transform vast amounts of threat data into clear, actionable, real-time knowledge. Our advanced cybersecurity solutions help security teams quickly track evolving attack patterns, discover critical weaknesses, and respond decisively with confidence.

Compliance and Validation in Security
We validate every layer of your cybersecurity stack from vulnerability scanners to incident response platforms to assure accuracy, interoperability, and adherence to regulations. Our rigorous practices help keep operations reliable and compliant.
Cutting-Edge Cyber Security Machine Learning & Analytics Tools To Boost Protection And Performance

Proactive Data-Driven Insights For Emerging Threats
Strengthen your defenses with actionable, intelligence-driven cyber threat data. From real-time attack signals to evolving vulnerability trends, our solutions help you stay a step ahead of emerging cyber risks.
- Comprehensive view of cyber threat signals.
- Dynamic vulnerability segmentation for smarter response.
- Cost-effective strategies to maximize security.
- AI-assisted incident detection and containment.
- Seamless integration with your IT ecosystem.

Data-Driven Predictive Analytics To Mitigate Risk
Analyze and prioritize complex cyber risks across your entire enterprise. From vulnerability scoring to emerging risk trends, our solutions empower you to manage risks proactively and effectively.
- Risk scoring driven by advanced algorithms.
- Automated vulnerability management and oversight.
- AI-assisted risk mitigation strategies.
- Cost-effective controls to safeguard assets.
- Scalable framework for enterprise-wide visibility.

Rapid Real-Time Action For Security Incidents
Analyze and prioritize complex cyber risks across your entire enterprise. From vulnerability scoring to emerging risk trends, our solutions empower you to manage risks proactively and effectively.
- Rapid incident identification and containment.
- Automated workflows for incident resolution.
- AI-assisted investigations and root-cause analysis.
- Cost-effective incident handling strategies.
- Seamless collaboration across security teams.

Innovative AI-Powered Solutions To Combat Cyberthreats
Transform your cybersecurity operations with cutting-edge technology. From threat hunting to policy automation, we help you innovate and adapt to a changing threat landscape.
- AI-assisted threat hunting techniques.
- Automated policy and control implementation.
- Scalable innovations to match growing risks.
- Cost-effective strategies for enterprise-wide security.
- Seamless integration with existing defenses.
Strengthening Security Resilience Through Intelligence Transformation

Targeted Intrusion Detection
Identify hidden cyber intrusions by analyzing large amounts of network data with advanced, automated techniques efficiently.
Proactive Risk Prevention
Strengthen defenses and lower vulnerability through tailored, data-informed protective strategies against growing cyberthreats accurately.
Comprehensive Access Control
Ensure tight oversight and policy adherence by managing credentials with robust authentication and authorization methods effectively.
Intuitive Security Dashboards
Leverage clear, actionable threat view designed for all team members, regardless of technical expertise or specialized roles.
Automated Incident Response
Reduce manual effort, cut incident resolution time, and minimize damage through automated containment and recovery protocols.
Custom Security Insights
Deploy tailored analytical platforms that align with unique enterprise risks and compliance goals for informed decisions.
Streamlined Processes For Cyber Security Data Analysis
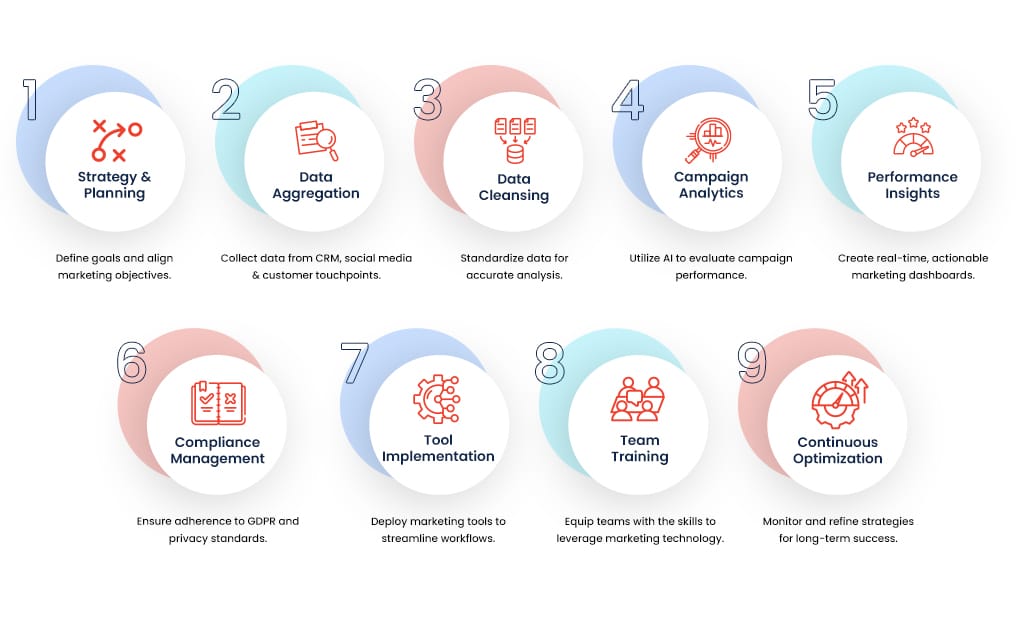
Innovative Cyber Protection Initiatives | Stronger Measures, Superior Outcomes
Comprehensive Threat Risk Evaluation
Anticipating cyber attacks and weaknesses with data-assisted models and scoring.
Advanced Breach Pattern Analysis
Uncovering attack methods through large-scale incident data and forensics.


Custom Security Measures
Designing defenses and controls based on enterprise profiles and vulnerability trends.
Response Improvement Metrics
Measuring incident resolution and containment with advanced performance indicators.

FAQ
How is AI strengthening cyber threat detection?
AI is strengthening cyber threat detection by analyzing vast amounts of network data, identifying abnormalities, and preventing attacks in real time.
What are the benefits of automation in response?
Automation streamlines incident response by reducing manual effort, speeding containment, and strengthening overall defenses against cyber attacks efficiently.
How does vulnerability scanning enhance security?
Vulnerability scanning proactively identifies weaknesses, assesses risks, and guides organizations to patch and harden their networks against future cyber intrusions.
Are enterprise credentials kept safe from theft?
Enterprise credentials are kept safe through strong encryption, multi-factor authentication, and policy controls to avoid unauthorized account takeover and fraud.
How is behavioral analysis used in cyber defenses?
Behavioral analysis assists in detecting deviations from normal activity, spotting insider risks, and addressing cyberthreats quickly and accurately across organizations.
What role does threat intelligence play in prevention?
Threat intelligence guides organizations to stay informed, anticipate attack methods, and implement protective measures against evolving cyber adversaries and tactics.














